Splunk is a big data platform handling large data sets; it can take huge amounts of data (structured and unstructured) and from them, through smart searches, obtain valuable information displayed through a web interface or report. It is most often used in IT security, compliance, IT Ops, but Splunk is extremely flexible, is machine learning and artificial intelligence enabled, and can be used for any purpose in almost any industry.
Thanks to Splunk's diversity it is used by 92 out of 100 "Fortune 100" companies; Splunkbase, Splunk's version of the app store, has over 2,400 install-ready applications and plugins. Also, for the past eight years in a row, Gartner has been declaring Splunk the leader in their famous Gartner Magic Quadrant.
Find out more about Splunk Professional Services in the brochure.
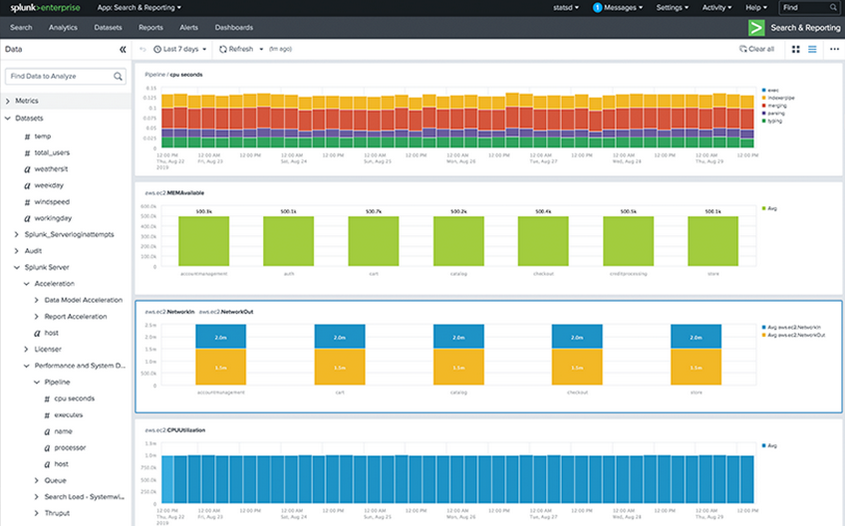
Data collection from any source (metrics, logs, clickstreams, sensors, arbitrary applications, hypervisors, containers, cloud...), running advanced searches, monitoring, and analysis. It provides operational insights across all industries and for any use and is the best option for obtaining useful information from a large amount of data.
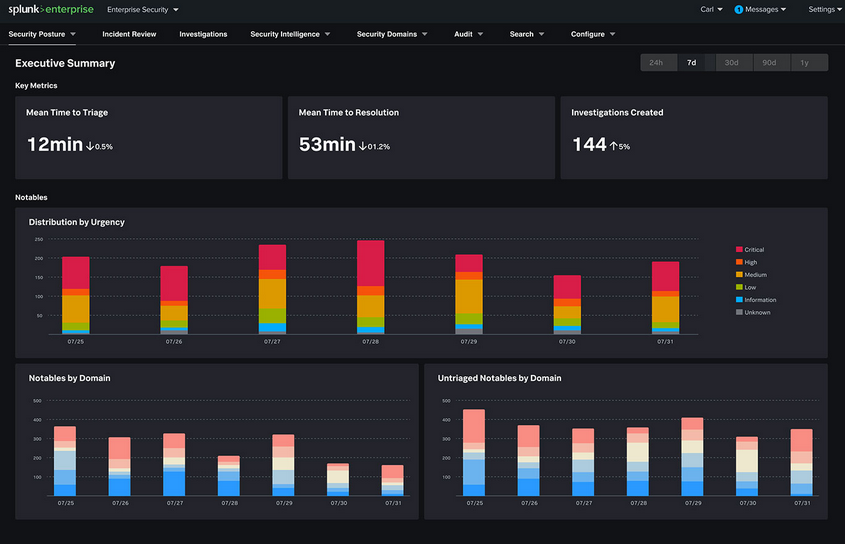
Splunk Enterprise Security is actually Splunk's SIEM (Security Information and Event Management) solution that allows security teams to quickly detect and respond to internal and external security threats. It provides visibility which is the first and basic step leading to improved security posture throughout the organization.
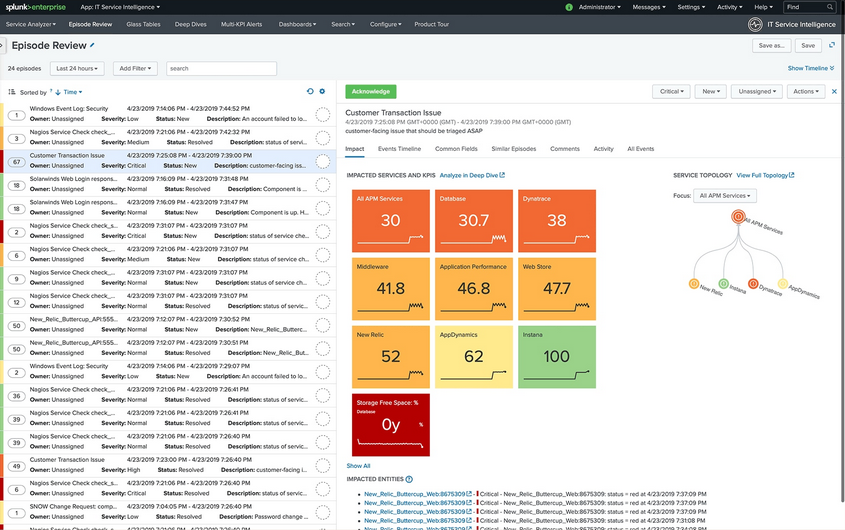
Splunk IT Service Intelligence is an analytical and IT management solution that allows IT teams to anticipate problems before they even occur. By using a large amount of data combined with machine learning, ITSI provides a perfect overview of all services with predictable analytics of events that will happen in the near future and reduces unplanned downtime by as much as 60 percent.
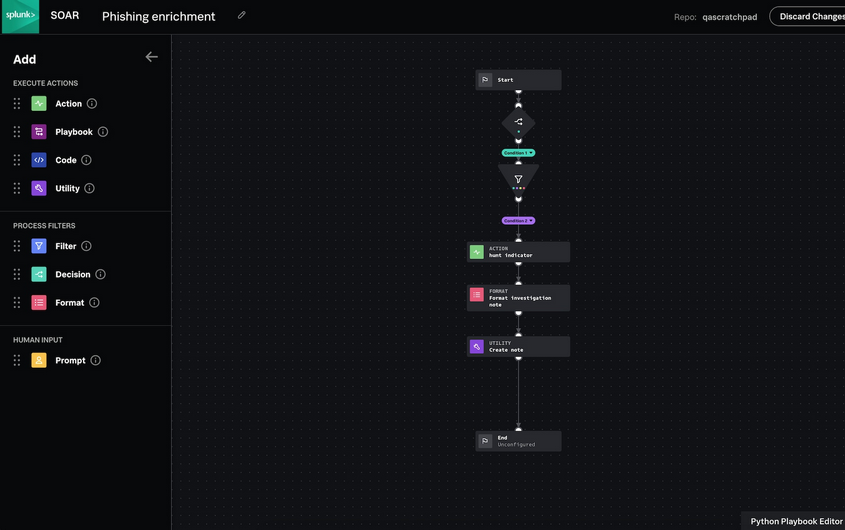
Splunk Security Orchestration, Automation and Response gives the modern SOC (Security Operations Center) the possibility to investigate and respond to security incidents in seconds, not in hours. Everything that should be routine, repetitive, predictable, SOAR takes over while leaving security analysts time to deal with more important things.
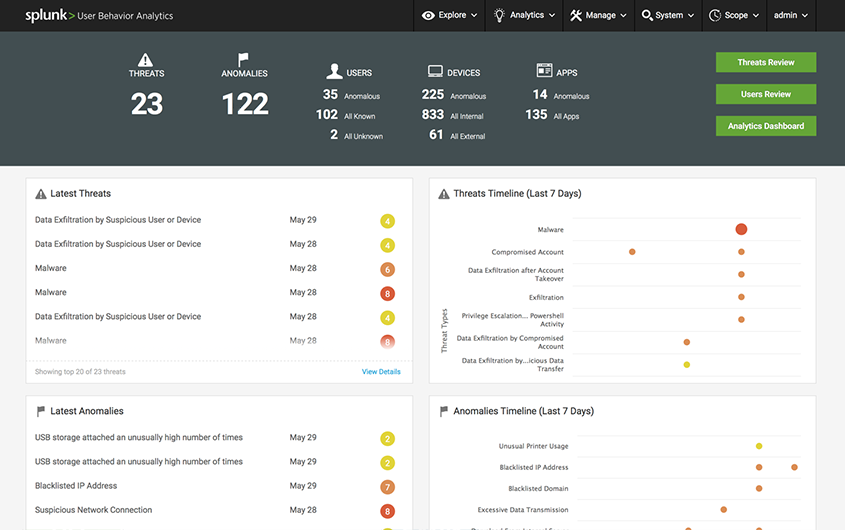
Splunk User Behavior Analytics helps organizations detect unknown and hidden security threats using machine learning that does not require human analysis or a variety of security signatures. Improves detection, increases the efficiency of security analysts, and makes life easier for SOC analysts, SIEM administrators, and other security personnel.
Splunk Cloud Platform and Splunk Security Cloud are actually Splunk Enterprise and Enterprise Security in the cloud, i.e. Splunk products that rely on their infrastructure and are sold as a service. It is still necessary to ingest all the data, optimize the whole system to work without problems and hitches, but the backend is taken care of by Splunk.
In addition to implementation, maintenance, and support, Infigo IS provides various Splunk-related services. After a lot of time spent with various Splunk-based systems, in all possible types of environments (often critical), with over 80 Splunk certificates held by our engineers and architects, we can easily call ourselves experts.
Therefore, we offer Splunk optimization services where we check the deployment effectiveness, search issues, diagnostics, structural issues, general optimization, and security review.
The SOC modernization and automation service includes advisory service, in-depth analysis of the current state of SOC, defining the development roadmap for the entire platform (includes technology, people, and processes), identifying gaps in the platform that must be addressed, and suggestions for improvement on every level.
The security review service includes a security monitoring review, alerting effectiveness, search review, and a comparison between the current security posture and the desired/possible one.
The educational service, which is usually included with the implementation, provides hands-on training that will teach participants not only the basics but also the tips'n'tricks that are the result of the hundreds of implementations we have done so far.